09.02
Technology Bytes
We RTFM so you don’t have to | 8-10 p.m. Wednesdays, 90.1FM KPFT in Houston
09.02
08.27
08.20
08.17
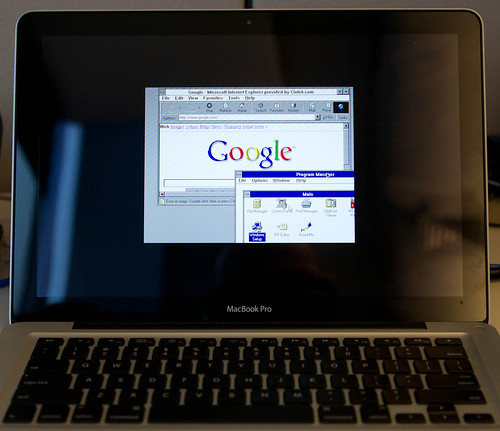
On a lark, I decided to see if I could get Windows 3.11 running in Parallels on the MacBook Pro. Installing DOS 6.22 and then Windows 3.11 was fairly straightforward after I located install disks on the Internet that were in .IMG format so that Parallels could mount them and install.
The more difficult part was getting TCP/IP up and running so that Windows 3.11 could access the Internet via the MacBook’s connection. All it took was downloading and installing TCP/IP-32 3.11b for Windows for Workgroups and configuring the TCP/IP stack for DHCP. After that I found a copy of Internet Explorer 5 which loaded right up.
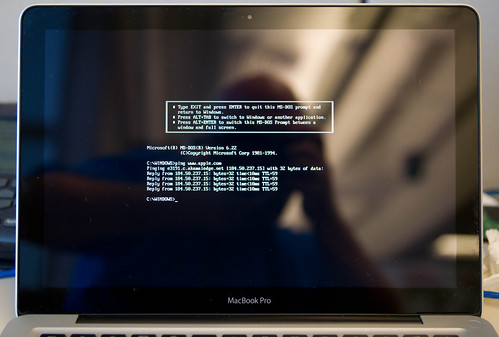
And to show this is not just a screen shot of a static page, here is a photo of the Macbook using Windows 3.11 to ping the Apple web site
Unfortunately I have been unable to find video drivers that will give me anything more than 16 colors at 800×600 resolution. And no sound, either. Still, it was a fun project!
08.05
08.04
 Via Mashable: Security Exploit Can Give Hackers Control of Your iPhone or iPad [WARNING]
Via Mashable: Security Exploit Can Give Hackers Control of Your iPhone or iPad [WARNING]
By just loading a PDF file on your iPhone, iPad or iPod Touch, you could be handing over complete access to your device in what could quickly become a major security breach.
As a recent Apple convert, I’m as guilty as the next geek in thinking that by using Apple products I’m immune to the exploits and hacks that seem synonymous with Windows. I work each day knee deep in Microsoft and I see more than my share of trojans, viruses and spyware. Despite our best efforts, we’re cleaning this crud off of our computers multiple times each week.
When I acquired my first Apple computer (the iMac) in June of 2009 I was giddy as a school girl, not only at the prospect of having new technology, but also in having something I was sure would be free of the pitfalls of the average Microsoft system.
To this day I don’t run anti-virus or security software on my iMac because I know that it is just not as vulnerable as the Windows computers I deal with every day.
But in my heart of hearts, I know that is changing. The Mashable story above is a testament to this fact.
Apple computers and other devices like the iPhone and the iPad are becoming less and less of a novelty and more the mainstream each and every day. Long time hold outs for Microsoft like myself have switched to Apple. And more are adopting every day. Add to the mix the growing number of Blackberry and Windows Mobile users who are ditching these devices in favor of the the iPhone to connect to corporate resources and it’s not hard to imagine that the hackers and sploiters will have no choice but to turn their dark skills to this platform with greater and greater zeal.
I have long recognized that Apple products are not immune to being exploited because they are flawless and so very secure. They have simply enjoyed what is commonly referred to as “security through obscurity.” Hunting hackers in the Windows world enjoyed a target rich environment where identities and banking info was theirs for the taking.
To Apple’s credit, they seem to be very responsive when vulnerabilities in their platform are identified. This is in stark contrast to Microsoft who seem slow to acknowledge and address security issues in a timely fashion.
Every time I see a story like the one above it reminds me that “vigilance” is still the watchword. One simply cannot assume they are invulnerable just because they use one particular product. Digital predators are everywhere and as Apple becomes a juicier target, there’s no reason to suspect the hackers won’t want to add their own “bite” to the popular product logo, metaphorically speaking.
I for one and going to install anti-virus software immediately and keep an eye on sites like Mashable/Apple and Cult Of Mac to make sure I stay informed.
—-
Jay Lee is the co-creator and host of Technology Bytes Radio. Lee is also author of Helpline for the Houston Chronicle.
07.29
07.22
07.15
We were joined in the studio by James Kendrick, mobile guru and blogger at JK On The Run for a lively discussion about smart phones and mobile computing.